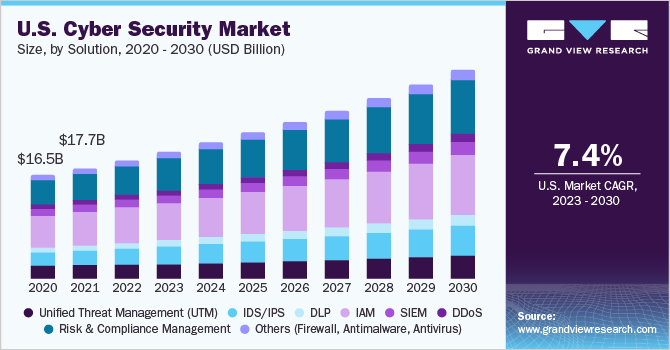
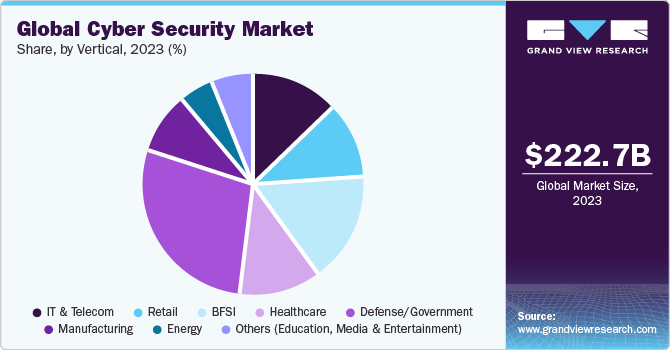
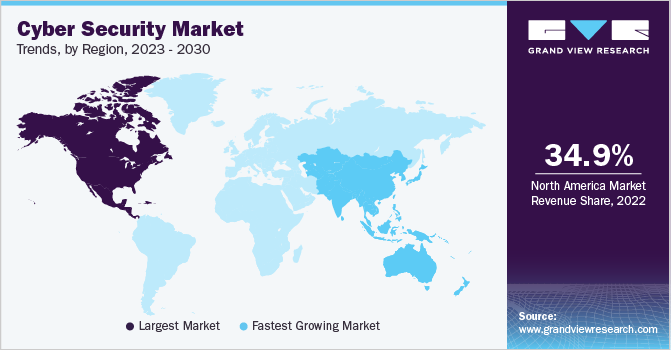
The global cyber security market is projected to grow at a 10.56% compound annual growth rate (CAGR) to over $273 billion by 2028 as businesses and organizations scramble to protect themselves against rising cyber threats. With high-profile hacks making headlines regularly, the need for robust cybersecurity solutions has never been more dire.
An independent cyber security consulting firm can help clients assess vulnerabilities, implement defense solutions, and respond to attacks. As breaches grow more complex, specialized expertise is in increasing demand.
This guide will walk you through how to start a cybersecurity company. Topics include market research to build a solid business plan, competitive analysis to learn about other cyber security companies in the area, registering an EIN, obtaining business insurance, and more.
1. Conduct Cybersecurity Company Market Research
Market research is an important part of starting any new cybersecurity company. It offers insight into your target market, trends in network security services, and competitors in the cybersecurity business sector. Market research adds a lot to a comprehensive business plan.
Some details you’ll learn about cybersecurity services through your market research include:
- As the number and complexity of cyberattacks increase, cybersecurity spending has skyrocketed.
- The rising need for cybersecurity services is fueling massive investment in new cybersecurity startups.
- For new market entrants, independent cyber security consulting presents a lucrative opportunity with enormous growth runways.
- As high-profile hacks make regular headlines, businesses are desperate for expertise in assessing vulnerabilities and implementing defenses.
- 70% of breaches target small businesses, most of whom lack robust in-house security teams to manage this complexity.
- Expect the talent war for elite security engineers and consultants to intensify as demand balloons.
- New entrants can differentiate through specialization, whether industry vertical, technology platform, compliance regulation, or security domain.
- Developing thought leadership and being seen as a trusted advisor earns enduring customer relationships and referrals.
- Launching any startup comes with risks.
- As cybercrime damages spiral exponentially, the escalating security requirements and massive talent shortage create ideal conditions for new consultancies to carve out a niche.
The soaring cyber security market provides unmatched opportunities for technically skilled entrepreneurs. By understanding client needs, specializing strategically, and positioning as a trusted advisor, cybersecurity consultancies can thrive while making the digital ecosystem safer.
2. Analyze the Competition
Understanding the competitive landscape is critical for any new business, especially in the crowded cybersecurity sector. Whether competing locally in a geographic region or more broadly online, meticulous competition analysis uncovers threats, opportunities, and strategic positioning.
Some ways to get to know competitors in your successful cybersecurity company include:
- For the regional competition, scour databases like Hoovers and Google Maps to identify cybersecurity consultancies in nearby locales by services rendered and client types.
- Study their websites closely, noting specific offerings, areas of expertise, clients served, pricing, and thought leadership.
- Interview former employees on Glassdoor to gain insider intelligence on competitive strengths, weaknesses, processes, and culture.
- Search press releases and news articles for product launches, strategic partners, new hires, and signs of scaling challenges.
- Attend industry events where competitors have speaking sessions or booths. Talk to their customers and observe prospect interactions.
- Cold call posing as a potential client and assessing sales approach and consultative needs analysis.
- For online competition, tools like SimilarWeb and Alexa provide visibility into website traffic volumes and sources, search visibility, and social media traction.
- Install their site analytics tools to track visit duration, bounce rates, and conversion funnels.
- Study online reviewer sentiment on Trustpilot and G2.
- Monitor relevant hashtags and competitors where they or customers are active on social media.
- Set Google News alerts mentioning brand names and leadership to capture announcements in real time.
By holistically analyzing regional peer cyber consultancies and the broader digital footprint of national players, astute competitive analysis crystallizes market positioning and formulas to outmaneuver rivals. It also steels strategic planning to capitalize on competitor weaknesses while building sustainable competitive advantage.
3. Costs to Start a Cyber Security Company Business
When starting any business, careful financial planning and cost analysis are imperative. For a cyber security consultancy, key start-up expenses span initial administrative requirements, office infrastructure and equipment, hiring first employees, marketing spending, and professional services.
Start-up Costs
- Administrative basics like business license registration, taxes, and insurance will likely cost between $500-$2,000 depending on location.
- Legal fees to incorporate the business properly typically range from $1,000-$5,000.
- Small commercial office spaces can run $1,000-$2,000 per month on shorter-term leases before investing in a long-term lease at $20-$30 per square foot annually.
In terms of cyber security office infrastructure, you’ll also face expenses for:
- A high-speed 200mbps fiber internet connection runs approximately $250 per month
- Network equipment like routers, switches, and firewall appliances average $2,500-$5,000 upfront
- New VoIP phone systems cost $500-$1,500 with low monthly plans thereafter
Ongoing Costs
- For furnished office build-outs, this entails $15,000-$60,000 for common spaces, conference rooms, private offices, and workstations.
- Leasing office equipment like printers/copiers requires little upfront cost at roughly $150-$300 monthly ongoing.
- Essential cybersecurity software packages for threat monitoring, network analysis, and endpoint security require upfront licensing fees from $1,000-$5,000 in addition to 15-25% annual support renewal costs.
- Virtual private network subscriptions to securely access client networks range from $30-$100 per user monthly.
- For 5-10 employees, mounting payroll expenses can quickly escalate from $400,000-$1.2M+ annually.
- Search, social and display ad campaigns range widely but plan on $15,000-$50,000 annually to gain traction.
- PR can be very effective for professional services positioning with monthly retainers between $5,000-$15,000 based on the agency selected.
- Event sponsorships run $5,000-$25,000 each for prominent cybersecurity conferences.
- Local event and trade group memberships to build community connections average under $5,000 per year.
- Outsourced accounting, legal, and recruiting fees to set up the business properly require $3,000-$10,000 as one-time start-up costs.
- These become ongoing monthly or quarterly expenses after launch around $1,500 and up per month collectively.
Expect between $100,000-$250,000 in start-up costs to launch even a modestly equipped cybersecurity consultancy with a small team – not counting office leasing needs. With fierce competition for contracts, having undercapitalized operations undermines credibility for a services firm unable to scale.
4. Form a Legal Business Entity
When starting a cybersecurity consultancy, the legal structure carrying liability protection is paramount given the data breach risks inherently faced working in this industry. While sole proprietorships and partnerships offer simplicity, your assets are fully exposed, an existential threat for cyber companies.
Sole Proprietorship
A sole proprietorship is easiest to form requiring little paperwork. There are low startup costs, no corporate taxes, and autonomy over decisions. However, the founder assumes unlimited financial and legal liability. With cybersecurity risks high, sole proprietorships fail to adequately shield personal assets like savings and property in litigation events.
Partnership
Partnerships allow multiple owners to combine assets and expertise to run a joint venture together. This expands startup capital and capabilities but still carries full unlimited liability for financial obligations to both partners and decision-making authority. Partnerships introduce potential disputes and require extensive legal guidance to implement effectively.
Limited Liability Company (LLC)
Conversely, a limited liability company (LLC) provides liability protection for owners while avoiding double taxation. LLCs have great flexibility in membership and profit distributions, with less recordkeeping than corporations. Startup costs range from $500-$2,000, with no limit on ownership. For consultancies facing outsourced risk advising clients, LLC status is vastly preferable shielding personal assets.
Corporation
S corporations also offer liability protection comparable to LLCs. However, with stricter IRS rules regarding ownership criteria and shareholder compensation, administrative costs run higher with more complex tax and compliance filings. Still, S corps provides a viable alternative to LLCs for some cyber consultancies seeking alternate investor incentives.
5. Register Your Business For Taxes
An employer identification number (EIN) serves as a unique tax ID to identify your business to the IRS and state agencies. As soon as you are legally forming a company, applying for an EIN should be one of your first steps.
An EIN is required to open any business bank accounts, apply for essential licenses and permits, file taxes properly each year, and hire employees down the road. It only takes a few minutes to obtain one and costs nothing directly through the IRS website.
To obtain your cybersecurity company’s EIN, simply:
- Navigate to the IRS EIN Assistant and select the option to “Apply Online Now” even if you plan to be the sole employee initially.
- Choose the default option to view the information in English, then click “Begin Application” to start the step-by-step EIN questionnaire.
- Answer each question prompted regarding the business type, ownership structure, activities performed, and responsible parties.
- Review all entries for accuracy, provide contact information, and assign an officer responsible for EIN communications going forward.
- Receive your EIN confirmation on screen and via the email provided immediately upon submitting successfully.
In addition to the federal EIN, double-check your individual state’s Department of Revenue website for any additional business tax certificates related to collecting and remitting sales taxes in your jurisdiction on consulting services provided.
6. Setup Your Accounting
With complex service contracts and various hacking liabilities faced, meticulous financial tracking is imperative for cybersecurity companies.
Accounting Software
Investing in QuickBooks accounting software centralizes invoices, expenses, payroll, and taxes in an intuitive platform. Supplemented by an experienced accountant, this builds airtight financial reporting to withstand IRS scrutiny. QuickBooks seamlessly syncs with time-tracking apps to import hours logged on client projects for invoicing.
Hire an Accountant
While QuickBooks handles much of the grunt work tracking daily financial flows, partnering with an accountant is still recommended for optimizing tax strategy and filings. A qualified accountant offers invaluable services like quarterly bookkeeping. Expect $1,000 to $5,000 in annual fees for an accountant depending on the activities required.
Open a Business Bank Account
Maintaining completely separate finances for your business is non-negotiable. Never commingle personal and company funds which muddy entity status. Always pay yourself and reimburse expenses through proper payroll and documented withdrawal procedures. Open a dedicated business checking account and credit card only used for company purchasing.
Apply for a Credit Card
Speaking of credit, business cards build commercial credit history tied to your EIN rather than the social security number used for consumer cards. Limits are lower initially but determined by business revenue and years in operation vs personal credit scores alone. Expect $1,000 to $10,000 for first business cards.
7. Obtain Licenses and Permits
When establishing any services business, proper licensing is critical for legal compliance and smooth operations. Find federal license information through the U.S. Small Business Administration. The SBA also offers a local search tool for state and city requirements.
At the federal level, while less common for services businesses, the Federal Trade Commission (FTC) mandates “Made in USA” product labeling disclosures to guide marketing claims. Properly communicating where offerings were developed helps avoid punitive misrepresentation violations.
For staff reliant on vehicles to perform onsite client assessments, blanket commercial auto insurance must sufficiently cover corporate-owned vehicles. Additionally, state departments of motor vehicles require obtaining supplementary commercial driver licenses (CDL) for employees driving larger trucks.
Local municipalities govern key facets of operating physical offices via zoning laws, facility occupancy limits, and inspection compliance. Commonly required permits cover building safety, electrical, plumbing, mechanical systems, fire prevention, food service, and disability access as examples.
Cyber consultancies additionally require specialized professional business licenses to legally provide certain high-expertise services restricted for consumer protection reasons without sufficient competency verification.
While specific occupational licenses vary by state, common professional credentials may encompass private investigation permits. IT security certifications and financial advisor qualifications depend on the niche cybersecurity disciplines engaged.
8. Get Business Insurance
Getting adequate business insurance is non-negotiable for a cybersecurity consultancy facing substantial data breach risks daily. Without proper coverage, a single event could permanently shutter operations. Here are three scenarios highlighting how lack of insurance devastates unprotected firms:
A breach originating from a vulnerability your team overlooked allows hackers to compromise several client networks simultaneously. Beyond immediate incident response and forensics expenses, you face massive legal liability for data and intellectual property loss.
On the way to meet a prospective client, your top sales executive gets into a major accident injuring the other driver. Their medical bills eclipse $250,000 and vehicle replacement runs $75,000. Without business auto insurance, your company assets get pursued to pay damages.
A disgruntled former employee launches a defamation and harassment social media crusade against your new consultancy. Lacking employment practices liability insurance means covering soaring legal expenses and defending the malicious attacks yourself.
Conversely, comprehensive business insurance policies greatly mitigate a wide spectrum of risks like these faced by cyber consultancies for modest premium investments. Core coverages to secure include general liability, commercial property, umbrella, commercial auto, workers’ compensation, E&O liability, cyber security, and employment practices.
The easiest way to get insured is by finding an independent broker to shop quotes across multiple carriers for your unique coverage needs. Expect some variation in pricing and risk appetite across insurers. Prioritize an agent taking time to understand your offerings, clients, office setup, and risk exposures over just chasing the cheapest base premium.
9. Create an Office Space
Establishing a professional office space lends credibility to consultancies selling high-value services. When meeting security-conscious prospects deciding between vendors, first impressions matter influencing trust and retention potential. Beyond client meetings, dedicated offices also provide infrastructure.
Coworking Office
Utilizing a WeWork flexible coworking space offers turnkey offices without huge upfront buildout costs. With sleek lounges to host small groups and reserved conference rooms for larger presentations, WeWork locations feature business-grade WiFi, printing/scanning, coffee bars, and front desk reception to handle mail/deliveries.
Commercial Office
For larger teams desiring custom cybersecurity infrastructure more aligned to in-house needs, commercial office leases enable fully customized buildouts. Expect to pay $20-$40 per square foot annually for spaces ranging from 1,500 sq ft to 5,000+ sq ft. This accommodates dedicated testing labs, server rooms secured via biometrics, exhibition spaces to showcase services, and training facilities.
Home Office
If launching initially as a solopreneur consultancy, operating from home eliminates commutes and brick-and-mortar expenses. Dedicate an isolated back room or finished basement to a home office for uninterrupted client calls and detailing penetration test reports. However, home offices lack credibility when meeting with enterprise prospects.
10. Source Your Equipment
Outfitting a capable cybersecurity office requires the latest computing hardware and software solutions. While buying brand new equipment is simplest, significant cost savings stem from buying quality refurbished gear, financing via leases or even renting certain assets.
Buy New
Purchasing new workstations and servers allows for fully customizing cutting-edge machines optimally configured for the security tools planned. Top vendors include Dell, HP, and Lenovo for workstations starting around $1,000 each. Servers scale from $2,500 entry-level models up to $15,000 for high-capacity data processing.
Buy Used
Buying used equipment through auction sites like eBay, or marketplaces such as Craigslist cuts acquisition costs 30-70% over new while still enabling robust Windows or Linux installations. Refurbished business-class laptops begin around $150 vs $500 new. Tower workstations start at $300 vs $1,000+ new.
Rent
For flexible equipment needs spanning client projects, specialized servers, and workstations prove more economical renting short-term rather than buying outright. National chains like Hertz and Sunbelt Rentals offer delivery/pickup with gear properly cleaned and awaiting use. Rental rates range from $100-$500 weekly for specialized assets like network analyzers and servers.
Lease
Leasing also subsidizes upfront capital for essential cybersecurity infrastructure as a fixed monthly cost over 3-5-year rental contracts. At term completion, newer updated models get rotated amid evolving equipment needs rather than maintaining the same liability-prone machines. Leasing facilitates keeping a technology edge in a continuously upgrading industry.
11. Establish Your Brand Assets
Establishing a professional brand builds awareness and trust for cybersecurity consultancies selling specialized services. From logos to websites, branding signals industry competency that new entities must earn when vying for lucrative enterprise contracts.
Get a Business Phone Number
Acquiring a business phone line on systems like RingCentral is essential even before launch. Listing the number across marketing materials associated with founding leadership gives prospective customers a vital lifeline for inquiries even pre-revenue. Expect basic digital phone plans from $30 monthly supporting call routing, voicemails, and CRM integrations.
Design a Logo
A polished Looka logo inheriting the consultancy name evokes the cybersecurity precision clients seek. Minimalist icons conveying data protection visually resonate without excessive complexity. Expect between $100-$500 sourcing custom designs matched to brand style guidelines.
Print Business Cards
Business card delivery remains vital when meeting highly targeted prospects at industry events or forging referral alliances. High-end Vistaprint cards with clean cyber graphics make memorable first impressions that spur follow-ups. When equipped with 500 cards running under $50, founders distributed judiciously, cards enable capturing contacts to fuel the sales pipeline post-conference.
Get a Domain Name
Securing CMS domains on Namecheap for $15 annually enables email addresses customers associate with reputable operations. Ideal naming resembles the consultancy name itself or close derivatives reinforcing capabilities i.e. CloudCyberDefense [dot] com.
Design a Website
Consultancies can quickly launch sites themselves via Wix website builders with hundreds of professional cybersecurity templates available. Expect around $300 annually running secure sites with lead gen forms to capture visitor inquiries. For more advanced custom designs, hiring specialized developers on Fiverr costs between $500-$5,000 based on complexity.
12. Join Associations and Groups
Tapping local cybersecurity associations, events, and online groups accelerates industry connections for fledgling consultancies seeking their first clients. By actively networking among peer firms and prospects, founders gain referrals, vet strategies and keep their fingers on the pulse of regional opportunities.
Local Associations
Joining established groups like the San Francisco Bay Area Information Systems Security Association opens access to hundreds of ethical hacker peers also honing skills or selling services. Expect memberships starting around $100 annually including newsletters, access to job boards, and discounted industry events. Regional affiliations build community visibility fast.
Meetups
Attending meetups facilitates connecting face-to-face with like-minded cybersecurity professionals in your locale. Sites like Meetup centralize tech gatherings searchable by specialization and location. Even informal happy hours allow for organic relationship building that bubbles up sales prospects through trust built over time.
Facebook Groups
With thousands of members, Facebook Groups enable broader industry networking beyond geography. Check out the Women in CyberSecurity and Cybersecurity for Beginners groups. Share expertise in answering member inquiries to establish thought leadership. Diplomatically promote services only when highly relevant to feed questions organically.
13. How to Market a Cyber Security Company Business
Marketing is the lifeline growing recognition for any consultancy. While credentials and expertise matter, an unknown brand fails to convert leads without visibility. A blend of digital promotion, community networking, and customer evangelism expands reach exponentially.

Personal Networking
Tap your inner circle first. Offer discounts for referrals within professional networks and local associations. Thank happy early customers by providing complimentary penetration testing for each new 5 contracts referred.
Digital Marketing
For digital tactics, focus on driving highly targeted traffic:
- Launch Google Ads campaigns optimized for conversion value, not clicks. Target senior security manager titles within a geographic radius. Expect $2-$5 per click averaging 5-10 clicks to generate solid inbound leads.
- Promote high-value blog content and videos organically on LinkedIn to establish thought leadership among 500+ connections. Activity expands your reach into their networks.
- Sponsor relevant Facebook groups and subreddits related to ethical hacking and penetration testing. Budget $100 per month testing cost per lead acquired.
- Create a YouTube channel answering common questions security managers face. Optimize metadata to rank for terms like “how to conduct a risk analysis audit”.
Traditional Marketing
Offline channels demanding time have high touch potential:
- Host a monthly CISO roundtable with IT security heads from corporations in your city to share stories and pain points. Position your team as peer experts.
- Get quoted as a cybersecurity expert in local business journals and relevant national press responding to newsworthy breaches.
- Speak at University infosec programs to inspire future talent while promoting capabilities.
The most effective customer acquisition melds digital efficiency with personalized relationship building offline. Earned media exposure and community giveback compound lead generation planting seeds for long-term partnerships.
14. Focus on the Customer
Providing white-glove customer service is pivotal for those in the cybersecurity industry. With advanced threats constantly evolving, clients rely on partners monitoring landscapes diligently to recommend ongoing solutions.
For example, emerging ransomware strains like REvil illustrated adaptation risks in mid-2021. Savvy consultants proactively briefed customers on detection gaps observed and suggested upgraded software to bolster resilience without additional spending.
Consultants immediately deployed scripts assessing customer exposure based on internet-facing assets detected. Reports quantified potential business impacts tied to exploited Java-based apps.
In both scenarios, leading with empathy and accountability focused on client security postures customers highly value. When consultants take ownership of vetting and explaining emerging threats transparently, this expertise gets recognized and rewarded with expanded business scope. Positive experiences drive referrals and renewals.
